Cybersecurity
Jump to our solution offerings
Your Challenges
Over the last years, Cybersecurity has become a predominant topic for business resilience in industry, services sectors and in government. Ransomware, distributed attacks rendering business-critical websites useless, data theft, and major reputation damages are risks to be countered. Espionage is a common threat in hitech and financial businesses. Every day we can read about new breaches, hacks, malware attacks or major cybersecurity risks. Trusted products from vendors like Microsoft, Cisco, Apple or Adobe reveal major vulnerabilities or even backdoors, putting the integrity and confidentiality of our valuable data at risk. Privacy concerns materialize as risks, just as millions of citizen, voter or customer records are exposed or abused.
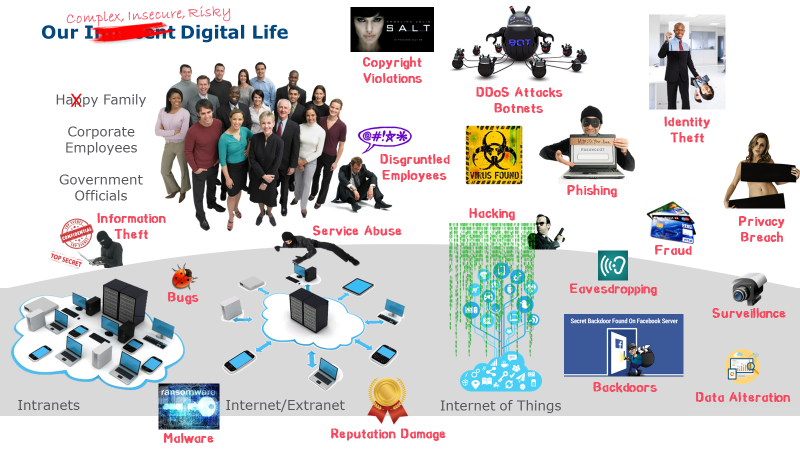
The average cost of incidents is estimated to range from $500 into millions – apart from permanent damages through the loss of intellectual property or reputational damages. In 2015, the impact of cybercrime was larger than from conventional crimes for the first time. Professional hacking enterprises start offering their services to parties interested in damaging competitors, obtaining confidential material, or afflicting the reputation of organizations and authorities. Social engineering clearly shows, however, that addressing these issues is not merely an IT subject.
Digital Transformation processes further increase the dependency of organizations on digital assets, processes and instruments with their integrity and availability. The resilience against cyberattacks and unintentional misuses of the IT infrastructure becomes a top priority for businesses to survive.
This is why organisations turn to highly scalable technology from the Big Data arena to efficiently cope with the vast amount of information relevant to Cybersecurity Operations Centers, but also broadly employ collaborative learning and Knowledge Management techniques to increase Cyberliteracy, Cyberawareness and Cybervigilance. Encryption on different levels, malware detection and a tight "need-to-know" approach lead to better base-level security.
Our Solutions
Adequate technological, organisational and strategic changes and continuous improvement processes ultimately create a collaborative intelligence that makes your business resilient against Cyberattacks. Cyber Vision provides solutions for the whole spectrum, from Identity and Trust Management to Threat and Vulnerabililites Management.
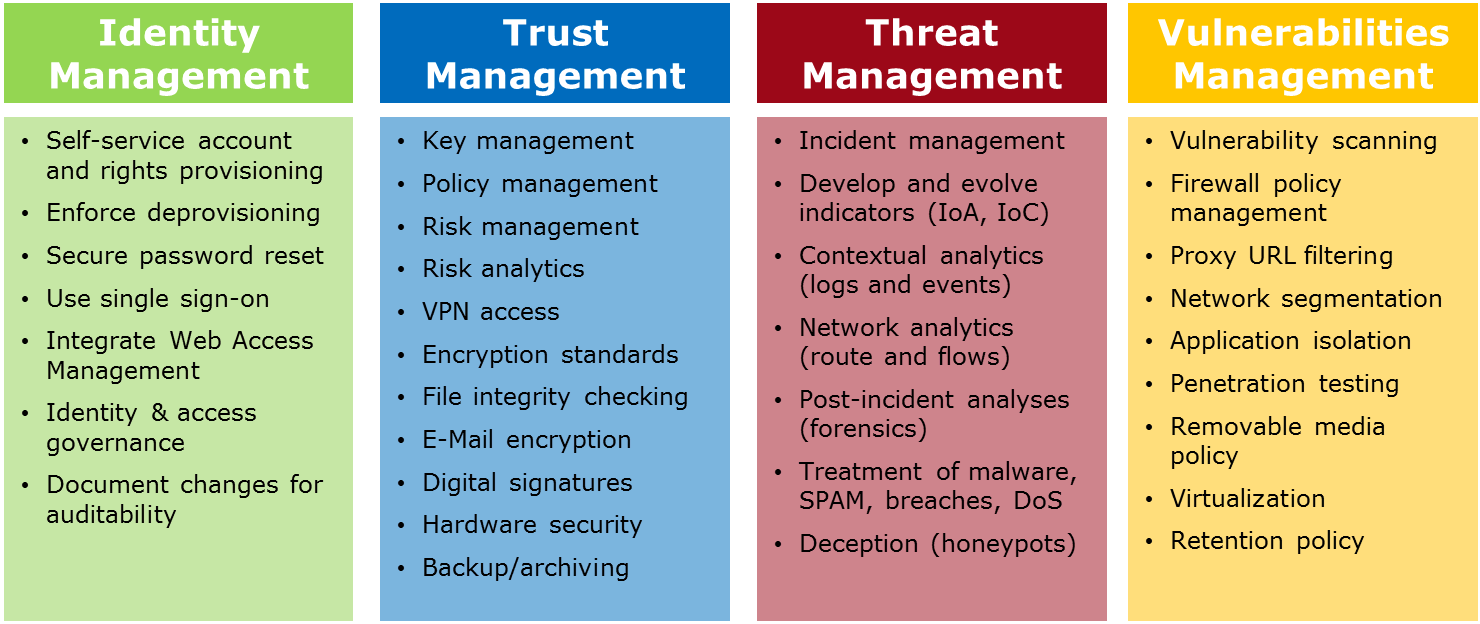
Apart from technological measures, we also help shape and implement a Cybersecurity strategy, enforced by policies and a pervasive Cybersecurity education. In many respects, Cybersecurity depends on an elaborate common sense - it is our task to sharpen this awareness and create a culture of resilience and vigilance.
